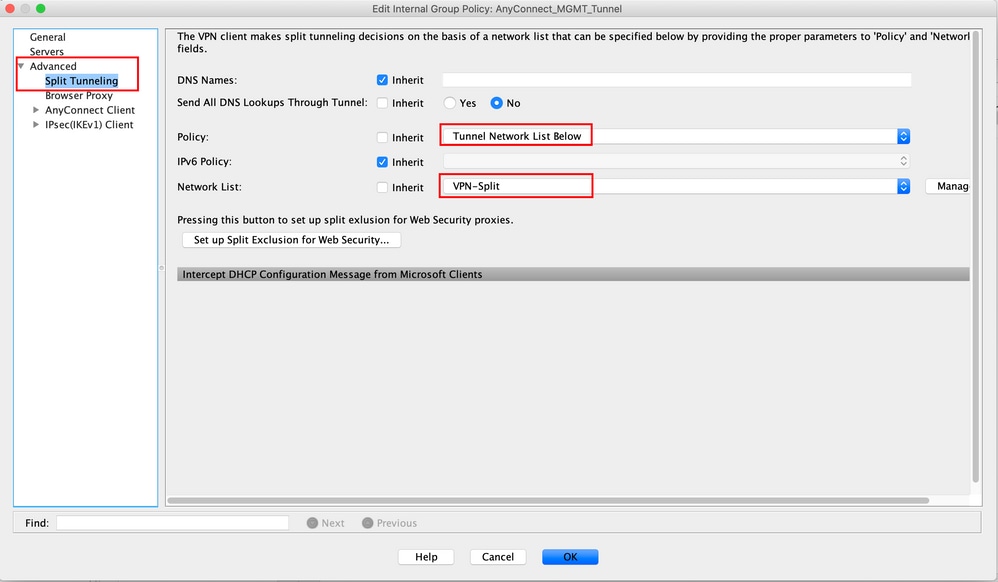
Cisco Vpn Server
Change is the vpn.acmeinc.com field. Update this to the new the new VPN server settings: vpn.betacorp.com. Now start the Cisco AnyConnect client and the default will now be updated. The big thing though is that it doesn't save the correct vpn.mydomain.com entry in the list of connections, so the user either has to manually type it in and click Connect or they have to go to the website and connect via the site itself.
- Cisco Vpn Server Configuration
- Anyconnect 'Untrusted Vpn Server Certificate - Cisco Community
- General Cisco VPN
- Cisco Vpn Server
- Cisco Vpn Server Address
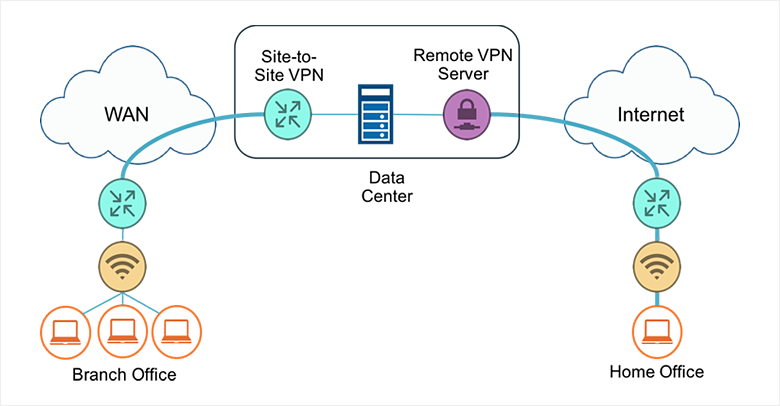
Two earlier tutorial articles discussed RouterOS, an open source operating system that can convert your generic PC into an advanced, enterprise-type router and LAN server.
In Part 1 of that series, you built the machine, installed the Linux-based software, and started setting it up.
In Part 2, you configured the DHCP server to manage the IP addresses, enabled NAT to share the Internet, and configured the wireless interface for Wi-Fi access.
Now that all the basic setup is done, you can play around with the features. In this part, you’ll tinker around with the VPN capabilities.
More specifically, you’ll set up a L2TP/IPsec VPN server.
Then users can remotely connect via the Internet to access files through the tunnel or to just use it to secure their connection on a public network.
Plus you’ll configure site-to-site tunnels, so all your networks are connected.
Configuring the VPN (L2TP) Server
First, make sure that you have the PPP package installed. If it is, you’ll have a menu for it on the console or WinBox interface.
Then you can follow these steps to get the server working using the WinBox utility:
- Click PPP and select the Secrets tab.
- Click the Plus button.
- Enter a Name and Password.
- Enter a Local Address (such as 1.1.1.1) and Remote Address (such as 1.1.1.2).
- Click OK.
Now you can enable the server. Follow these steps:
- On the main PPP window, select the Interface tab.
- Click the L2TP Server button.
- Mark the Enabled checkbox and click OK.
Now you need to add an IPSec peer. Follow these steps:
- Click IP > IPsec and select the Peer tab.
- Click the Plus button.
- Make sure that the Auth Methodis Pre-Shared Key.
- For Secret, enter a password to serve as the pre-shared key secret. You'll input this later when configuring Windows.
- Verify that the Hash Algorithm is sha and the EncryptionAlgorithm is 3des, which are used by default in Windows.
- Mark the Generate Policy checkbox.
The Network Policy Server (NPS) extension for Azure allows organizations to safeguard Remote Authentication Dial-In User Service (RADIUS) client authentication using cloud-based Azure AD Multi-Factor Authentication (MFA), which provides two-step verification.
This article provides instructions for integrating NPS infrastructure with MFA by using the NPS extension for Azure. This process enables secure two-step verification for users who attempt to connect to your network by using a VPN.
Network Policy and Access Services gives organizations the ability to:
Assign a central location for the management and control of network requests to specify:
Who can connect
What times of day connections are allowed
The duration of connections
The level of security that clients must use to connect
Rather than specify policies on each VPN or Remote Desktop Gateway server, do so after they're in a central location. The RADIUS protocol is used to provide centralized Authentication, Authorization, and Accounting (AAA).
Establish and enforce Network Access Protection (NAP) client health policies that determine whether devices are granted unrestricted or restricted access to network resources.
Provide a way to enforce authentication and authorization for access to 802.1x-capable wireless access points and Ethernet switches.For more information, see Network Policy Server.
To enhance security and provide a high level of compliance, organizations can integrate NPS with Azure AD Multi-Factor Authentication to ensure that users use two-step verification to connect to the virtual port on the VPN server. For users to be granted access, they must provide their username and password combination and other information that they control. This information must be trusted and not easily duplicated. It can include a cell phone number, a landline number, or an application on a mobile device.
Prior to the availability of the NPS extension for Azure, customers who wanted to implement two-step verification for integrated NPS and MFA environments had to configure and maintain a separate MFA server in an on-premises environment. This type of authentication is offered by Remote Desktop Gateway and Azure Multi-Factor Authentication Server using RADIUS.
With the NPS extension for Azure, organizations can secure RADIUS client authentication by deploying either an on-premises based MFA solution or a cloud-based MFA solution.
Authentication flow
When users connect to a virtual port on a VPN server, they must first authenticate by using a variety of protocols. The protocols allow the use of a combination of user name and password and certificate-based authentication methods.
In addition to authenticating and verifying their identity, users must have the appropriate dial-in permissions. In simple implementations, dial-in permissions that allow access are set directly on the Active Directory user objects.
In simple implementations, each VPN server grants or denies access based on policies that are defined on each local VPN server.
In larger and more scalable implementations, the policies that grant or deny VPN access are centralized on RADIUS servers. In these cases, the VPN server acts as an access server (RADIUS client) that forwards connection requests and account messages to a RADIUS server. To connect to the virtual port on the VPN server, users must be authenticated and meet the conditions that are defined centrally on RADIUS servers.
Cisco Vpn Server Configuration
When the NPS extension for Azure is integrated with the NPS, a successful authentication flow results, as follows:
- The VPN server receives an authentication request from a VPN user that includes the username and password for connecting to a resource, such as a Remote Desktop session.
- Acting as a RADIUS client, the VPN server converts the request to a RADIUS Access-Request message and sends it (with an encrypted password) to the RADIUS server where the NPS extension is installed.
- The username and password combination is verified in Active Directory. If either the username or password is incorrect, the RADIUS Server sends an Access-Reject message.
- If all conditions, as specified in the NPS Connection Request and Network Policies, are met (for example, time of day or group membership restrictions), the NPS extension triggers a request for secondary authentication with Azure AD Multi-Factor Authentication.
- Azure AD Multi-Factor Authentication communicates with Azure Active Directory, retrieves the user's details, and performs the secondary authentication by using the method that's configured by the user (cell phone call, text message, or mobile app).
- When the MFA challenge is successful, Azure AD Multi-Factor Authentication communicates the result to the NPS extension.
- After the connection attempt is both authenticated and authorized, the NPS where the extension is installed sends a RADIUS Access-Accept message to the VPN server (RADIUS client).
- The user is granted access to the virtual port on the VPN server and establishes an encrypted VPN tunnel.
Prerequisites
This section details the prerequisites that must be completed before you can integrate MFA with the VPN. Before you begin, you must have the following prerequisites in place:
- VPN infrastructure
- Network Policy and Access Services role
- Azure AD Multi-Factor Authentication license
- Windows Server software
- Libraries
- Azure Active Directory (Azure AD) synced with on-premises Active Directory
- Azure Active Directory GUID ID
VPN infrastructure
This article assumes that you have a working VPN infrastructure that uses Microsoft Windows Server 2016 and that your VPN server is currently not configured to forward connection requests to a RADIUS server. In the article, you configure the VPN infrastructure to use a central RADIUS server.
If you do not have a working VPN infrastructure in place, you can quickly create one by following the guidance in numerous VPN setup tutorials that you can find on the Microsoft and third-party sites.
The Network Policy and Access Services role
Network Policy and Access Services provides the RADIUS server and client functionality. This article assumes that you have installed the Network Policy and Access Services role on a member server or domain controller in your environment. In this guide, you configure RADIUS for a VPN configuration. Install the Network Policy and Access Services role on a server other than your VPN server.
For information about installing the Network Policy and Access Services role service Windows Server 2012 or later, see Install a NAP Health Policy Server. NAP is deprecated in Windows Server 2016. For a description of best practices for NPS, including the recommendation to install NPS on a domain controller, see Best practices for NPS.
Azure AD MFA License
A license is required for Azure AD Multi-Factor Authentication, and it is available through an Azure AD Premium, Enterprise Mobility + Security, or a Multi-Factor Authentication stand-alone license. Consumption-based licenses for Azure AD MFA such as per user or per authentication licenses are not compatible with the NPS extension. For more information, see How to get Azure AD Multi-Factor Authentication. For testing purposes, you can use a trial subscription.
Windows Server software
The NPS extension requires Windows Server 2008 R2 SP1 or later, with the Network Policy and Access Services role installed. All the steps in this guide were performed with Windows Server 2016.
Libraries
The following libraries are installed automatically with the NPS extension:
If the Microsoft Azure Active Directory PowerShell Module is not already present, it is installed with a configuration script that you run as part of the setup process. There is no need to install the module ahead of time if it is not already installed.
Azure Active Directory synced with on-premises Active Directory
To use the NPS extension, on-premises users must be synced with Azure Active Directory and enabled for MFA. This guide assumes that on-premises users are synced with Azure Active Directory via Azure AD Connect. Instructions for enabling users for MFA are provided below.
For information about Azure AD Connect, see Integrate your on-premises directories with Azure Active Directory.
Azure Active Directory GUID ID
To install the NPS extension, you need to know the GUID of the Azure Active Directory. Instructions for finding the GUID of the Azure Active Directory are provided in the next section.
Configure RADIUS for VPN connections
If you have installed the NPS role on a member server, you need to configure it to authenticate and authorize the VPN client that requests VPN connections.
This section assumes that you have installed the Network Policy and Access Services role but have not configured it for use in your infrastructure.
Note
If you already have a working VPN server that uses a centralized RADIUS server for authentication, you can skip this section.
Register Server in Active Directory
To function properly in this scenario, the NPS server must be registered in Active Directory.
Open Server Manager.
In Server Manager, select Tools, and then select Network Policy Server.
In the Network Policy Server console, right-click NPS (Local), and then select Register server in Active Directory. Select OK two times.
Leave the console open for the next procedure.
Use wizard to configure the RADIUS server
You can use a standard (wizard-based) or advanced configuration option to configure the RADIUS server. This section assumes that you're using the wizard-based standard configuration option.
In the Network Policy Server console, select NPS (Local).
Under Standard Configuration, select RADIUS Server for Dial-Up or VPN Connections, and then select Configure VPN or Dial-Up.
In the Select Dial-up or Virtual Private Network Connections Type window, select Virtual Private Network Connections, and then select Next.
In the Specify Dial-Up or VPN Server window, select Add.
In the New RADIUS client window, provide a friendly name, enter the resolvable name or IP address of the VPN server, and then enter a shared secret password. Make the shared secret password long and complex. Record it, because you'll need it in the next section.
Select OK, and then select Next.
In the Configure Authentication Methods window, accept the default selection (Microsoft Encrypted Authentication version 2 [MS-CHAPv2]) or choose another option, and select Next.
Note
If you configure Extensible Authentication Protocol (EAP), you must use either Microsoft Challenge-Handshake Authentication Protocol (CHAPv2) or Protected Extensible Authentication Protocol (PEAP). No other EAP is supported.
In the Specify User Groups window, select Add, and then select an appropriate group. If no group exists, leave the selection blank to grant access to all users.
Select Next.
In the Specify IP Filters window, select Next.
In the Specify Encryption Settings window, accept the default settings, and then select Next.
In the Specify a Realm Name window, leave the realm name blank, accept the default setting, and then select Next.
In the Completing New Dial-up or Virtual Private Network Connections and RADIUS clients window, select Finish.
Verify the RADIUS configuration
This section details the configuration you created by using the wizard.
On the Network Policy Server, in the NPS (local) console, expand RADIUS Clients, and then select RADIUS Clients.
In the details pane, right-click the RADIUS client that you created, and then select Properties. The properties of your RADIUS client (the VPN server) should be like those shown here:
Select Cancel.
On the Network Policy Server, in the NPS (local) console, expand Policies, and then select Connection Request Policies. The VPN Connections policy is displayed as shown in the following image:
Under Policies, select Network Policies. You should see a Virtual Private Network (VPN) Connections policy that resembles the policy shown in the following image:
Configure your VPN server to use RADIUS authentication
In this section, you configure your VPN server to use RADIUS authentication. The instructions assume that you have a working configuration of a VPN server but have not configured it to use RADIUS authentication. After you configure the VPN server, confirm that your configuration is working as expected.
Note
If you already have a working VPN server configuration that uses RADIUS authentication, you can skip this section.
Configure authentication provider
On the VPN server, open Server Manager.
In Server Manager, select Tools, and then select Routing and Remote Access.
In the Routing and Remote Access window, right-click <server name> (local), and then select Properties.
In the <server name> (local) Properties window, select the Security tab.
On the Security tab, under Authentication provider, select RADIUS Authentication, and then select Configure.
In the RADIUS Authentication window, select Add.
In the Add RADIUS Server window, do the following:
a. In the Server name box, enter the name or IP address of the RADIUS server that you configured in the previous section.
b. For the Shared secret, select Change, and then enter the shared secret password that you created and recorded earlier.
c. In the Time-out (seconds) box, enter a value of 30.
The timeout value is necessary to allow enough time to complete the second authentication factor. Some VPNs or regions require time-out settings greater than 30 seconds to prevent users from receiving multiple phone calls. If users do experience this issue, increase the Time-out (seconds) value in increments of 30 seconds until the issue doesn't reoccur.Select OK.
Test VPN connectivity
In this section, you confirm that the VPN client is authenticated and authorized by the RADIUS server when you attempt to connect to the VPN virtual port. The instructions assume that you are using Windows 10 as a VPN client.
Note
If you already configured a VPN client to connect to the VPN server and have saved the settings, you can skip the steps related to configuring and saving a VPN connection object.
On your VPN client computer, select the Start button, and then select the Settings button.
In the Windows Settings window, select Network & Internet.
Select VPN.
Select Add a VPN connection.
In the Add a VPN connection window, in the VPN provider box, select Windows (built-in), complete the remaining fields, as appropriate, and then select Save.
Go to Control Panel, and then select Network and Sharing Center.
Select Change adapter settings.
Right-click the VPN network connection, and then select Properties.
In the VPN properties window, select the Security tab.
On the Security tab, ensure that only Microsoft CHAP Version 2 (MS-CHAP v2) is selected, and then select OK.
Right-click the VPN connection, and then select Connect.
In the Settings window, select Connect.
A successful connection appears in the Security log, on the RADIUS server, as Event ID 6272, as shown here:
Troubleshooting RADIUS
Assume that your VPN configuration was working before you configured the VPN server to use a centralized RADIUS server for authentication and authorization. If the configuration was working, it is likely that the issue is caused by a misconfiguration of the RADIUS server or the use of an invalid username or password. For example, if you use the alternate UPN suffix in the username, the sign-in attempt might fail. Use the same account name for best results.
To troubleshoot these issues, an ideal place to start is to examine the Security event logs on the RADIUS server. To save time searching for events, you can use the role-based Network Policy and Access Server custom view in Event Viewer, as shown here. 'Event ID 6273' indicates events where the NPS denied access to a user.
Configure Multi-Factor Authentication
For assistance configuring users for Multi-Factor Authentication see the articles Planning a cloud-based Azure AD Multi-Factor Authentication deployment and Set up my account for two-step verification
Install and configure the NPS extension
This section provides instructions for configuring VPN to use MFA for client authentication with the VPN server.
Note
The REQUIRE_USER_MATCH registry key is case sensitive. All values must be set in UPPER CASE format.
After you install and configure the NPS extension, all RADIUS-based client authentication that is processed by this server is required to use MFA. If all your VPN users are not enrolled in Azure AD Multi-Factor Authentication, you can do either of the following:
Set up another RADIUS server to authenticate users who are not configured to use MFA.
Create a registry entry that allows challenged users to provide a second authentication factor if they are enrolled in Azure AD Multi-Factor Authentication.
Create a new string value named REQUIRE_USER_MATCH in HKLMSOFTWAREMicrosoftAzureMfa, and set the value to TRUE or FALSE.
If the value is set to TRUE or is blank, all authentication requests are subject to an MFA challenge. If the value is set to FALSE, MFA challenges are issued only to users who are enrolled in Azure AD Multi-Factor Authentication. Use the FALSE setting only in testing or in production environments during an onboarding period.
Obtain the Azure Active Directory tenant ID
As part of the configuration of the NPS extension, you must supply administrator credentials and the ID of your Azure AD tenant. To get the tenant ID, complete the following steps:
Sign in to the Azure portal as the global administrator of the Azure tenant.
In the Azure portal menu, select Azure Active Directory, or search for and select Azure Active Directory from any page.
On the Overview page, the Tenant information is shown. Next to the Tenant ID, select the Copy icon, as shown in the following example screenshot:
Install the NPS extension
The NPS extension must be installed on a server that has the Network Policy and Access Services role installed and that functions as the RADIUS server in your design. Do not install the NPS extension on your VPN server.
Download the NPS extension from Microsoft Download Center.
Copy the setup executable file (NpsExtnForAzureMfaInstaller.exe) to the NPS server.
On the NPS server, double-click NpsExtnForAzureMfaInstaller.exe and, if you are prompted, select Run.
In the NPS Extension For Azure AD MFA Setup window, review the software license terms, select the I agree to the license terms and conditions check box, and then select Install.
In the NPS Extension For Azure AD MFA Setup window, select Close.
Configure certificates for use with the NPS extension by using a PowerShell script
To ensure secure communications and assurance, configure certificates for use by the NPS extension. The NPS components include a Windows PowerShell script that configures a self-signed certificate for use with NPS.
The script performs the following actions:
- Creates a self-signed certificate.
- Associates the public key of the certificate to the service principal on Azure AD.
- Stores the certificate in the local machine store.
- Grants the network user access to the certificate's private key.
- Restarts the NPS service.
If you want to use your own certificates, you must associate the public key of your certificate with the service principal on Azure AD, and so on.
To use the script, provide the extension with your Azure Active Directory administrative credentials and the Azure Active Directory tenant ID that you copied earlier. The account must be in the same Azure AD tenant as you wish to enable the extension for. Run the script on each NPS server where you install the NPS extension.
Run Windows PowerShell as an administrator.
At the PowerShell command prompt, enter cd 'c:Program FilesMicrosoftAzureMfaConfig', and then select Enter.
At the next command prompt, enter .AzureMfaNpsExtnConfigSetup.ps1, and then select Enter. The script checks to see whether the Azure AD PowerShell module is installed. If it is not installed, the script installs the module for you.
If you get a security error due to TLS, enable TLS 1.2 using the
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12command from your PowerShell prompt.After the script verifies the installation of the PowerShell module, it displays the Azure Active Directory PowerShell module sign-in window.
Enter your Azure AD administrator credentials and password, and then select Sign in.
At the command prompt, paste the tenant ID that you copied earlier, and then select Enter.
The script creates a self-signed certificate and performs other configuration changes. The output is like that in the following image:
Reboot the server.
Verify the configuration

To verify the configuration, you must establish a new VPN connection with the VPN server. After you've successfully entered your credentials for primary authentication, the VPN connection waits for the secondary authentication to succeed before the connection is established, as shown below.
Anyconnect 'Untrusted Vpn Server Certificate - Cisco Community
If you successfully authenticate with the secondary verification method that you previously configured in Azure AD MFA, you are connected to the resource. However, if the secondary authentication is unsuccessful, you are denied access to the resource.
In the following example, the Microsoft Authenticator app on a Windows Phone provides the secondary authentication:
After you've successfully authenticated by using the secondary method, you are granted access to the virtual port on the VPN server. Because you were required to use a secondary authentication method by using a mobile app on a trusted device, the sign-in process is more secure than if it were using only a username and password combination.
View Event Viewer logs for successful sign-in events
To view successful sign-in events in the Windows Event Viewer logs query the Windows Security log, on the NPS server, by entering the following PowerShell command:
You can also view the security log or the Network Policy and Access Services custom view, as shown here:
General Cisco VPN
On the server where you installed the NPS extension for Azure AD Multi-Factor Authentication, you can find Event Viewer application logs that are specific to the extension at Application and Services LogsMicrosoftAzureMfa.
Troubleshooting guide
If the configuration is not working as expected, begin troubleshooting by verifying that the user is configured to use MFA. Have the user connect to the Azure portal. If the user is prompted for secondary authentication and can successfully authenticate, you can eliminate an incorrect configuration of MFA as an issue.
If MFA is working for the user, review the relevant Event Viewer logs. The logs include the security event, Gateway operational, and Azure AD Multi-Factor Authentication logs that are discussed in the previous section.
An example of a security log that displays a failed sign-in event (event ID 6273) is shown here:
A related event from the Azure AD Multi-Factor Authentication log is shown here:
To do advanced troubleshooting, consult the NPS database format log files where the NPS service is installed. The log files are created in the %SystemRoot%System32Logs folder as comma-delimited text files. For a description of the log files, see Interpret NPS Database Format Log Files.
The entries in these log files are difficult to interpret unless you export them to a spreadsheet or a database. You can find many Internet Authentication Service (IAS) parsing tools online to assist you in interpreting the log files. The output of one such downloadable shareware application is shown here:
Cisco Vpn Server
To do additional troubleshooting, you can use a protocol analyzer such as Wireshark or Microsoft Message Analyzer. The following image from Wireshark shows the RADIUS messages between the VPN server and the NPS.
For more information, see Integrate your existing NPS infrastructure with Azure AD Multi-Factor Authentication.
Cisco Vpn Server Address
Next steps
